What is Web Application Vulnerability Scanning?
Web Application Vulnerability Scanning
Vulnerability scanning is a necessary component of a vulnerability management program. Because web applications are heavily used and can be exploited by hackers, their security must be a top priority. A vulnerability scan can identify vulnerabilities and help your organization prevent a breach before it happens. In addition to identifying the vulnerabilities present in your web applications, it can also help you develop stronger security controls.
Depending on the size of your company’s application and how much security you require, you can choose from many web application vulnerability scanners. Some of these tools are free, while others are more expensive. Choosing the right one requires some research. Typically, a web application vulnerability scans costs between $4500 and $6,000 a year. The cost can also vary depending on the length of the contract and the number of apps you’re scanning.
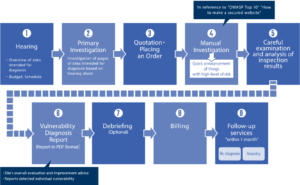
Vulnerability scanning is an important process that needs to be performed regularly. Web application vulnerability scanning is not a one-time event; it is a continuous process that requires consistent, regular scanning. The easier a vulnerability scanner is to use, the better. A single vulnerability can wreck an otherwise successful business.
What is Web Application Vulnerability Scanning?
Web application vulnerability scanners perform security tests against web applications, looking for vulnerabilities that are not previously known. These scanners are also known as Dynamic Application Security Testing (DAST) tools. Various commercial and open source web application vulnerability scanners are available on the market. There are also OWASP Benchmarks, which measure the effectiveness of vulnerability detection tools.
A web application vulnerability scanner should be able to find vulnerabilities in web applications that can allow hackers to gain access to your website. It should also be able to detect XSS, SQL injection, and other common vulnerabilities. The tool should also allow you to run security tests against a wide range of other web applications. It should be easy to use even for novices.
A web vulnerability scanner provides reports in various levels of detail, including specific request and response, allowing a knowledgeable user to confirm a particular vulnerability. Some scanners also use site mapping to determine whether an application is vulnerable. They also use crawling techniques to find out what user paths are and how they are impacted.
In some cases, web application vulnerability scanning is done by using test accounts with limited access to sensitive data and harmful operations. Many applications have special workflows that are presented to users for the first time they log in. This means that the results from a test account that was used initially will be different from those from a user account that has been used for a while.
The most common vulnerability scanners apply DAST or IAST methodologies to find vulnerabilities in web applications. The results of such tests may be useful to developers, as they can identify potential threats and implement remediation measures. In addition to this, vulnerability scanners often integrate with QA and DevOps processes.